Tability is a cheatcode for goal-driven teams. Set perfect OKRs with AI, stay focused on the work that matters.
What are It Security Analyst OKRs?
The OKR acronym stands for Objectives and Key Results. It's a goal-setting framework that was introduced at Intel by Andy Grove in the 70s, and it became popular after John Doerr introduced it to Google in the 90s. OKRs helps teams has a shared language to set ambitious goals and track progress towards them.
Formulating strong OKRs can be a complex endeavor, particularly for first-timers. Prioritizing outcomes over projects is crucial when developing your plans.
We've tailored a list of OKRs examples for It Security Analyst to help you. You can look at any of the templates below to get some inspiration for your own goals.
If you want to learn more about the framework, you can read our OKR guide online.
The best tools for writing perfect It Security Analyst OKRs
Here are 2 tools that can help you draft your OKRs in no time.
Tability AI: to generate OKRs based on a prompt
Tability AI allows you to describe your goals in a prompt, and generate a fully editable OKR template in seconds.
- 1. Create a Tability account
- 2. Click on the Generate goals using AI
- 3. Describe your goals in a prompt
- 4. Get your fully editable OKR template
- 5. Publish to start tracking progress and get automated OKR dashboards
Watch the video below to see it in action 👇
Tability Feedback: to improve existing OKRs
You can use Tability's AI feedback to improve your OKRs if you already have existing goals.
- 1. Create your Tability account
- 2. Add your existing OKRs (you can import them from a spreadsheet)
- 3. Click on Generate analysis
- 4. Review the suggestions and decide to accept or dismiss them
- 5. Publish to start tracking progress and get automated OKR dashboards
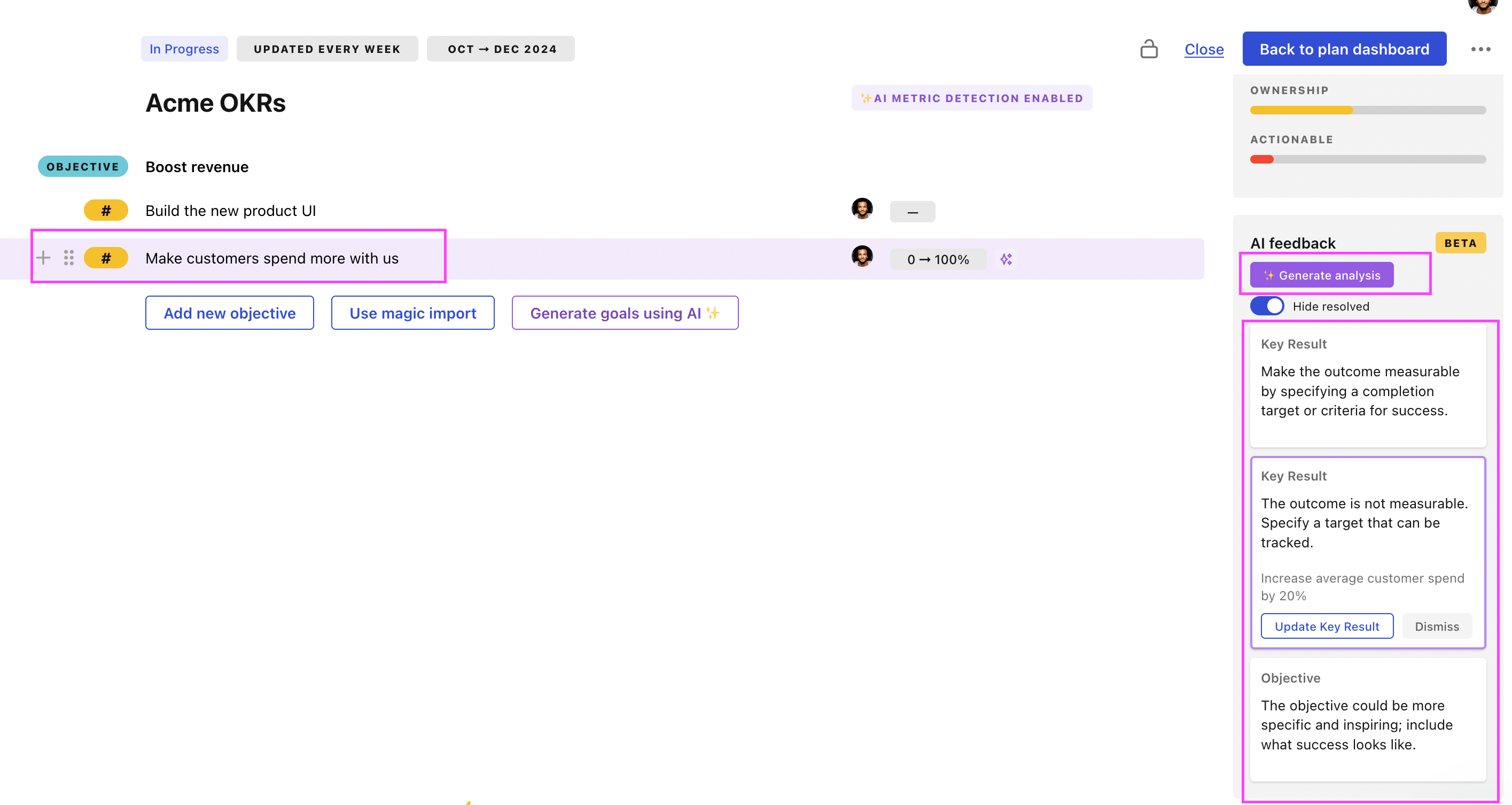
Tability will scan your OKRs and offer different suggestions to improve them. This can range from a small rewrite of a statement to make it clearer to a complete rewrite of the entire OKR.
It Security Analyst OKRs examples
You'll find below a list of Objectives and Key Results templates for It Security Analyst. We also included strategic projects for each template to make it easier to understand the difference between key results and projects.
Hope you'll find this helpful!
OKRs to fully integrate Abnormal Security tool in SecOps ecosystem with IT partnership
ObjectiveFully integrate Abnormal Security tool in SecOps ecosystem with IT partnership
KREliminate 75% of detected security threats using the Abnormal Security tool by term end
Use Abnormal Security tool to neutralize threats
Identify and analyze detected security threats
Complete training on Abnormal Security tool
KRAchieve 90% Abnormal Security tool deployment across all IT infrastructure within quarter
Identify systems not yet using the Abnormal Security tool
Develop a staggered implementation schedule for all remaining infrastructure
Monitor and report on deployment progress weekly
KRConduct 3 collaborative training sessions to foster seamless use and understanding among SecOps team
Prepare training materials and exercises
Schedule 3 collaborative training sessions
Determine training topics relevant to SecOps team
OKRs to seamless integration and deployment of Productiv SaaS application
ObjectiveSeamless integration and deployment of Productiv SaaS application
KRIdentify and reduce shadow IT instances by 25% using the Productiv app
Assemble team to identify current shadow IT instances
Establish plan to reduce shadow IT by 25%
Utilize Productiv app for IT management analysis
KRValidate Productiv SaaS's compatibility with our systems by the end of week 1
Execute a small-scale compatibility test using Productiv SaaS
Identify our system's requirements and Productiv SaaS's specifications
Analyze test results and articulate findings
KRSuccessfully train 90% of the IT team on managing the Productiv SaaS application
Identify key features in the Productiv SaaS application for training focus
Develop comprehensive training program for IT team members
Monitor and evaluate training progress and effectiveness
OKRs to implement phase one of privilege access management tool replacement
ObjectiveImplement phase one of privilege access management tool replacement
KRDevelop detailed transition plan to ensure zero service disruptions
Schedule and communicate transition plan to all stakeholders
Develop contingency strategies addressing identified risks
Identify critical services and potential disruption risks
KRTrain 70% of IT staff on the operation of selected new access management tools
Organize and implement the scheduled training sessions
Choose appropriate access management tools for training
Identify 70% of IT staff requiring access management training
KRIdentify and assess five potential replacement tools, determining suitability by end of quarter
Research and list five potential replacement tools
Evaluate each tool's effectiveness and suitability
Present findings and recommendation by the deadline
OKRs to strengthen cybersecurity to reduce incidents by 50%
ObjectiveImprove cybersecurity to minimize incidents
KRCreate and test updated incident response and disaster recovery procedures
Develop and document updated incident response and disaster recovery plans
Identify stakeholders and their roles in incident response and disaster recovery
Train employees on updated procedures and conduct mock drills
Evaluate effectiveness of updated procedures and make necessary adjustments
KRIncrease the number of cybersecurity training sessions attended by employees
Regularly communicate the importance of cybersecurity to employees
Develop engaging cybersecurity training content
Offer incentives for attending cybersecurity training sessions
Implement mandatory cybersecurity training for all employees
KRConduct two external security audits to identify vulnerabilities
Review and implement audit findings
Monitor security vulnerabilities and take appropriate actions
Share relevant security information
Hire third-party audit firms
KRImplement two-factor authentication for high-risk data access
Implement authentication for high-risk data
Choose two-factor authentication method
Train employees on new authentication method
Test and monitor authentication effectiveness
OKRs to enhance proactive investigation through expanded log analysis
ObjectiveEnhance proactive investigation through expanded log analysis
KRLower the average response time to identified threats by 20%
Seek professional consultation on response strategy
Implement advanced threat detection software
Train staff to swiftly respond to threats
KRTrain the team on the new tool to improve threat identification by 40%
Organize a comprehensive training session on the new tool
Measure improvements in threat identification post-training
Select team members to participate in threat identification training
KRImplement advance log analysis tool to automatically identify and flag potential threats
Research and select an advanced log analysis tool
Train IT team on threat identification and response
Install and configure the chosen tool
OKRs to implement and maintain a comprehensive data protection program
ObjectiveStrengthen data protection program
KREnsure compliance with relevant data protection laws and regulations
Regularly review and update data protection practices
Develop and implement policies and procedures for compliance
Identify all applicable data protection regulations
Train employees on data protection laws and regulations
KRConduct a thorough risk assessment and mitigation plan
create contingency plan
develop mitigation strategies
assess likelihood and impact
identify potential risks
KRImplement regular employee training and awareness programs
Schedule regular training sessions
Identify training needs and design a program
Evaluate program effectiveness and make necessary improvements
Encourage employee participation and reward progress
KRRegularly review and update data protection policies and procedures
Train employees on updated policies and procedures
Document all data protection policies and procedures
Regularly audit adherence to policies and procedures
Assign responsibility for policy and procedure review and updates
OKRs to become a computer security expert
ObjectiveBecome a computer security expert
KRSuccessfully pass the Certified Ethical Hacker (CEH) exam with a score of 80% or higher
KRDevelop and execute a comprehensive security project, receiving positive feedback from industry experts
Collaborate with industry experts to gather insights and recommendations for improving security measures
Regularly monitor and evaluate the effectiveness of implemented security measures to ensure ongoing protection
Develop and implement robust security protocols and controls across all systems and processes
Conduct a thorough assessment of current security vulnerabilities and risks
KRComplete at least two online courses on computer security, scoring above 90% in each
Ensure mastery of course materials and aim to score above 90% in assessments
Devote dedicated hours per week to studying and completing the online courses
Research and identify two reputable online courses for computer security
Enroll in the selected online courses on computer security
KRImplement and manage effective security measures on personal computer resulting in zero malware incidents
Install a reliable antivirus software program on the personal computer
Enable automatic software updates for the operating system and all installed applications
Avoid clicking on suspicious links or downloading files from untrustworthy sources
Regularly update the antivirus software to ensure the latest protection against malware
OKRs to enhance network security measures
ObjectiveStrengthen network security
KRConduct regular vulnerability assessments and remediation
KRImplement two-factor authentication on all devices
KRDecrease number of successful network breaches by 50%
KRTrain 100% of employees on cybersecurity best practices
OKRs to implement cutting-edge bot detection technologies for website data
ObjectiveImplement cutting-edge bot detection technologies for website data
KRAchieve 95% accuracy rate in detecting bots using newly implemented technologies
Continuously refine and update the models deployed
Test algorithms with diverse sets of data
Implement new machine learning algorithms for bot detection
KRIntegrate and test 3 selected bot detection technologies on our website
Choose three suitable bot detection technologies for our website
Conduct thorough testing to ensure effectiveness
Implement these technologies into our site's backend
KRIdentify and study 10 new bot detection methods from industry research
Analyze each method's pros, cons, and applicability
Select 10 recent industry research on bot detection methods
Prepare a report summarizing findings
OKRs to establish robust security controls for DHS/ATO and NATO contracts
ObjectiveEstablish robust security controls for DHS/ATO and NATO contracts
KRConduct quarterly maintenance on all the security controls and document findings
Document observations and any maintenance executed
Review all security control systems thoroughly
Perform necessary maintenance on security controls
KRImplement 5 new security measures aligned with DHS/ATO requirements by a 100%
Identify potential security measures that align with DHS/ATO requirements
Implement and test the newly identified security measures
Review existing security measures for any DHS/ATO non-compliance
KRAchieve zero security breaches related to the NATO contracts information
Implement strong encryption on all NATO-related digital communication
Train staff in counter-intelligence and data protection practices
Regularly perform rigorous security audits and fix vulnerabilities
It Security Analyst OKR best practices
Generally speaking, your objectives should be ambitious yet achievable, and your key results should be measurable and time-bound (using the SMART framework can be helpful). It is also recommended to list strategic initiatives under your key results, as it'll help you avoid the common mistake of listing projects in your KRs.
Here are a couple of best practices extracted from our OKR implementation guide 👇
Tip #1: Limit the number of key results
Focus can only be achieve by limiting the number of competing priorities. It is crucial that you take the time to identify where you need to move the needle, and avoid adding business-as-usual activities to your OKRs.
We recommend having 3-4 objectives, and 3-4 key results per objective. A platform like Tability can run audits on your data to help you identify the plans that have too many goals.
Tip #2: Commit to weekly OKR check-ins
Having good goals is only half the effort. You'll get significant more value from your OKRs if you commit to a weekly check-in process.
Being able to see trends for your key results will also keep yourself honest.
Tip #3: No more than 2 yellow statuses in a row
Yes, this is another tip for goal-tracking instead of goal-setting (but you'll get plenty of OKR examples above). But, once you have your goals defined, it will be your ability to keep the right sense of urgency that will make the difference.
As a rule of thumb, it's best to avoid having more than 2 yellow/at risk statuses in a row.
Make a call on the 3rd update. You should be either back on track, or off track. This sounds harsh but it's the best way to signal risks early enough to fix things.
Save hours with automated It Security Analyst OKR dashboards
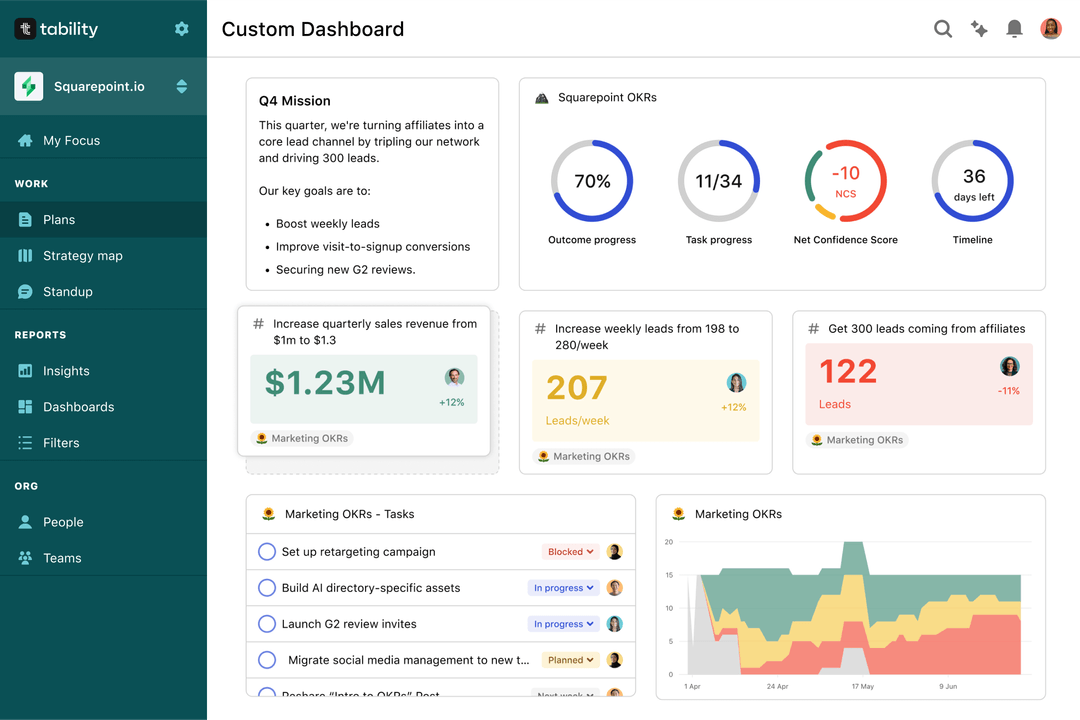
Your quarterly OKRs should be tracked weekly if you want to get all the benefits of the OKRs framework. Reviewing progress periodically has several advantages:
- It brings the goals back to the top of the mind
- It will highlight poorly set OKRs
- It will surface execution risks
- It improves transparency and accountability
Most teams should start with a spreadsheet if they're using OKRs for the first time. Then, you can move to Tability to save time with automated OKR dashboards, data connectors, and actionable insights.
How to get Tability dashboards:
- 1. Create a Tability account
- 2. Use the importers to add your OKRs (works with any spreadsheet or doc)
- 3. Publish your OKR plan
That's it! Tability will instantly get access to 10+ dashboards to monitor progress, visualise trends, and identify risks early.
More It Security Analyst OKR templates
We have more templates to help you draft your team goals and OKRs.
OKRs to successfully lead the organisation of online event "12 Days of Christmas"
OKRs to enhance compliance and engagement through sales audit
OKRs to enhance response communication quality
OKRs to enhance cloud architecture expertise and expand project portfolio
OKRs to prepare for a Series A funding
OKRs to successfully merge two websites with optimized SEO strategy