OKR template to become a computer security expert
Your OKR template
The first objective focuses on preparation for, and passing, the Certified Ethical Hacker (CEH) exam with at least an 80% score. The CEH, a highly recognized certification, will contribute greatly in affirming the individual's expertise in computer security. This objective is therefore crucial to the overall aim.
Another objective is to create and successfully complete a comprehensive security project that garners positive feedback from industry experts. This involves engaging with professionals, measuring the efficacy of implemented security measures, and developing and instituting robust protocols throughout all systems and processes. This objective requires proactive efforts in networking and meticulous execution of ongoing security procedures.
The final objectives entail completing at least two online courses with a score of 90% or higher and implementing effective security measures on the owner's PC, resulting in zero malware incidents. This will further cement knowledge and practical skills in computer security, while the latter objective offers an opportunity to directly apply learned skills in a personal context.
ObjectiveBecome a computer security expert
KRSuccessfully pass the Certified Ethical Hacker (CEH) exam with a score of 80% or higher
KRDevelop and execute a comprehensive security project, receiving positive feedback from industry experts
Collaborate with industry experts to gather insights and recommendations for improving security measures
Regularly monitor and evaluate the effectiveness of implemented security measures to ensure ongoing protection
Develop and implement robust security protocols and controls across all systems and processes
Conduct a thorough assessment of current security vulnerabilities and risks
KRComplete at least two online courses on computer security, scoring above 90% in each
Ensure mastery of course materials and aim to score above 90% in assessments
Devote dedicated hours per week to studying and completing the online courses
Research and identify two reputable online courses for computer security
Enroll in the selected online courses on computer security
KRImplement and manage effective security measures on personal computer resulting in zero malware incidents
Install a reliable antivirus software program on the personal computer
Enable automatic software updates for the operating system and all installed applications
Avoid clicking on suspicious links or downloading files from untrustworthy sources
Regularly update the antivirus software to ensure the latest protection against malware
How to edit and track OKRs with Tability
You'll probably want to edit the examples in this post, and Tability is the perfect tool for it.
Tability is an AI-powered platform that helps teams set better goals, monitor execution, and get help to achieve their objectives faster.
With Tability you can:
- Use AI to draft a complete set of OKRs in seconds
- Connect your OKRs and team goals to your project
- Automate reporting with integrations and built-in dashboard
Instead of having to copy the content of the OKR examples in a doc or spreadsheet, you can use Tability’s magic importer to start using any of the examples in this page.
The import process can be done in seconds, allowing you to edit OKRs directly in a platform that knows how to manage and track goals.
Step 1. Sign up for a free Tability account
Go tohttps://tability.app/signup and create your account (it's free!)
Step 2. Create a plan
Follow the steps after your onboarding to create your first plan, you should get to a page that looks like the picture below.
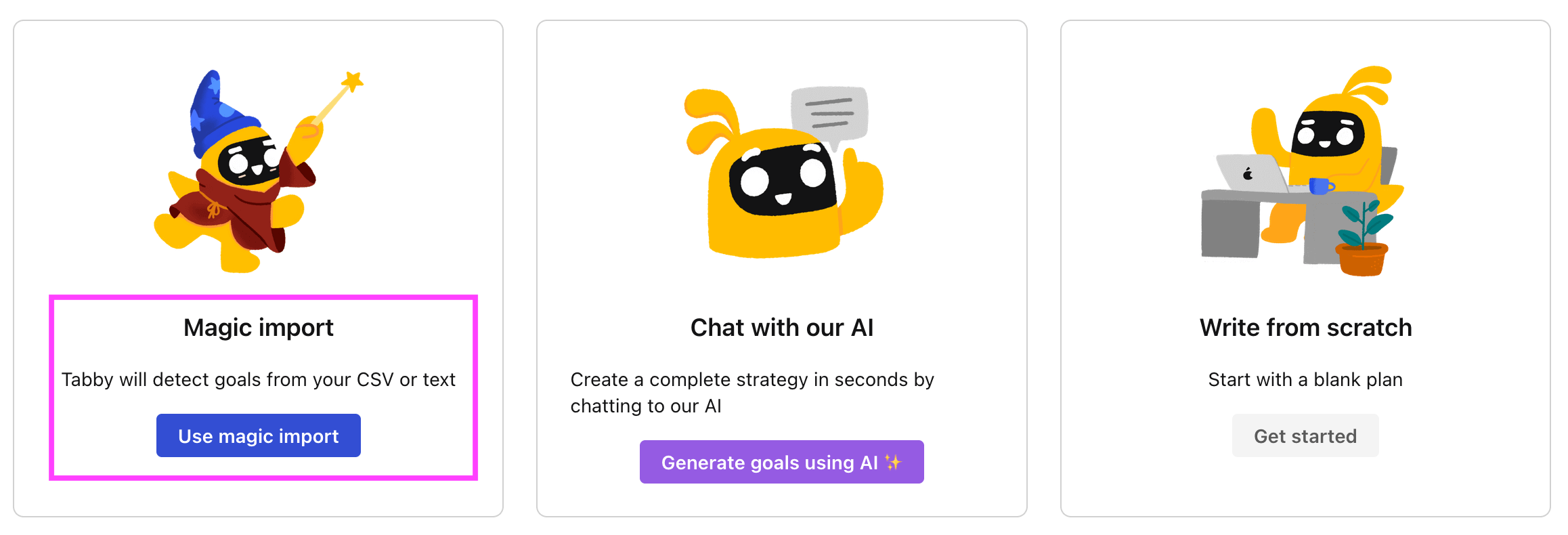
Step 3. Use the magic importer
Click on Use magic import to open up the Magic Import modal.
Now, go back to the OKR examples, and click on Copy on the example that you’d like to use.
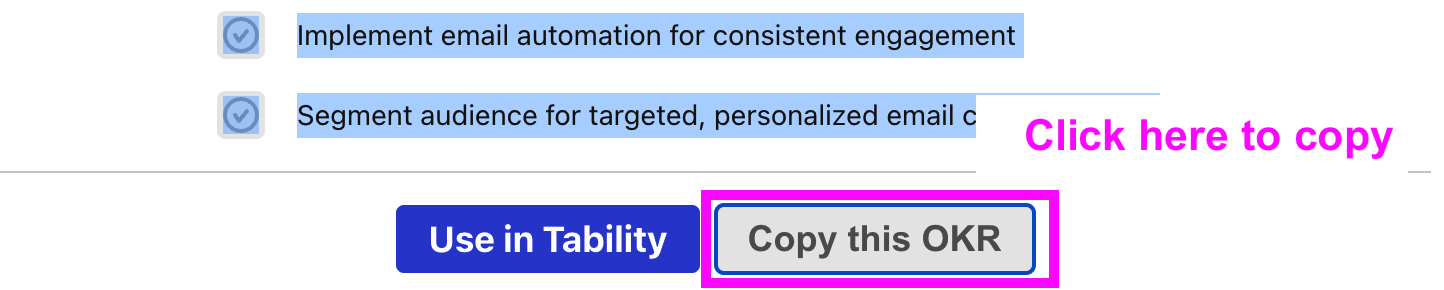
Paste the content in the text import section. Don’t worry about the formatting, Tability’s AI will be able to parse it!
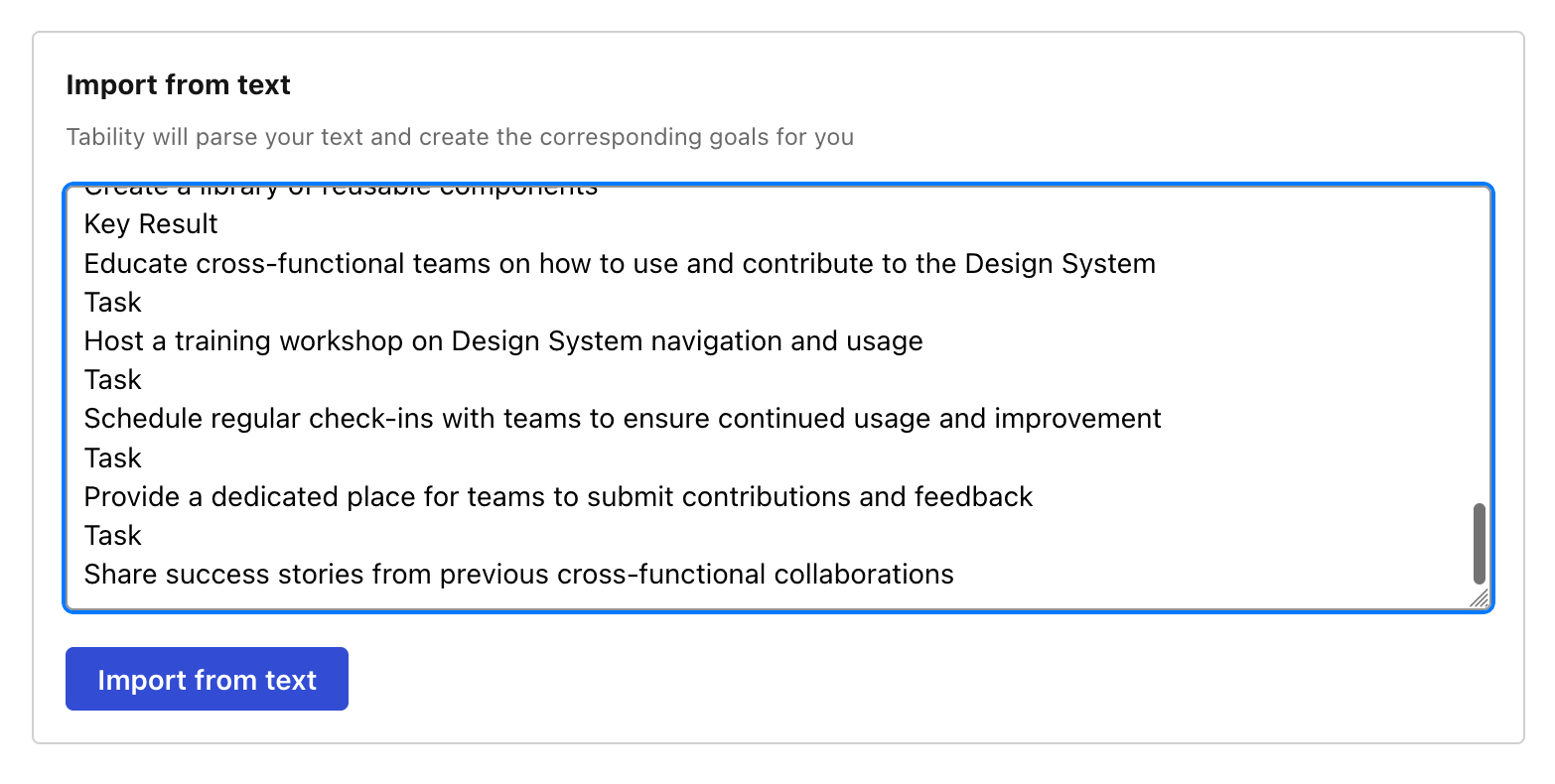
Now, just click on Import from text and let the magic happen.
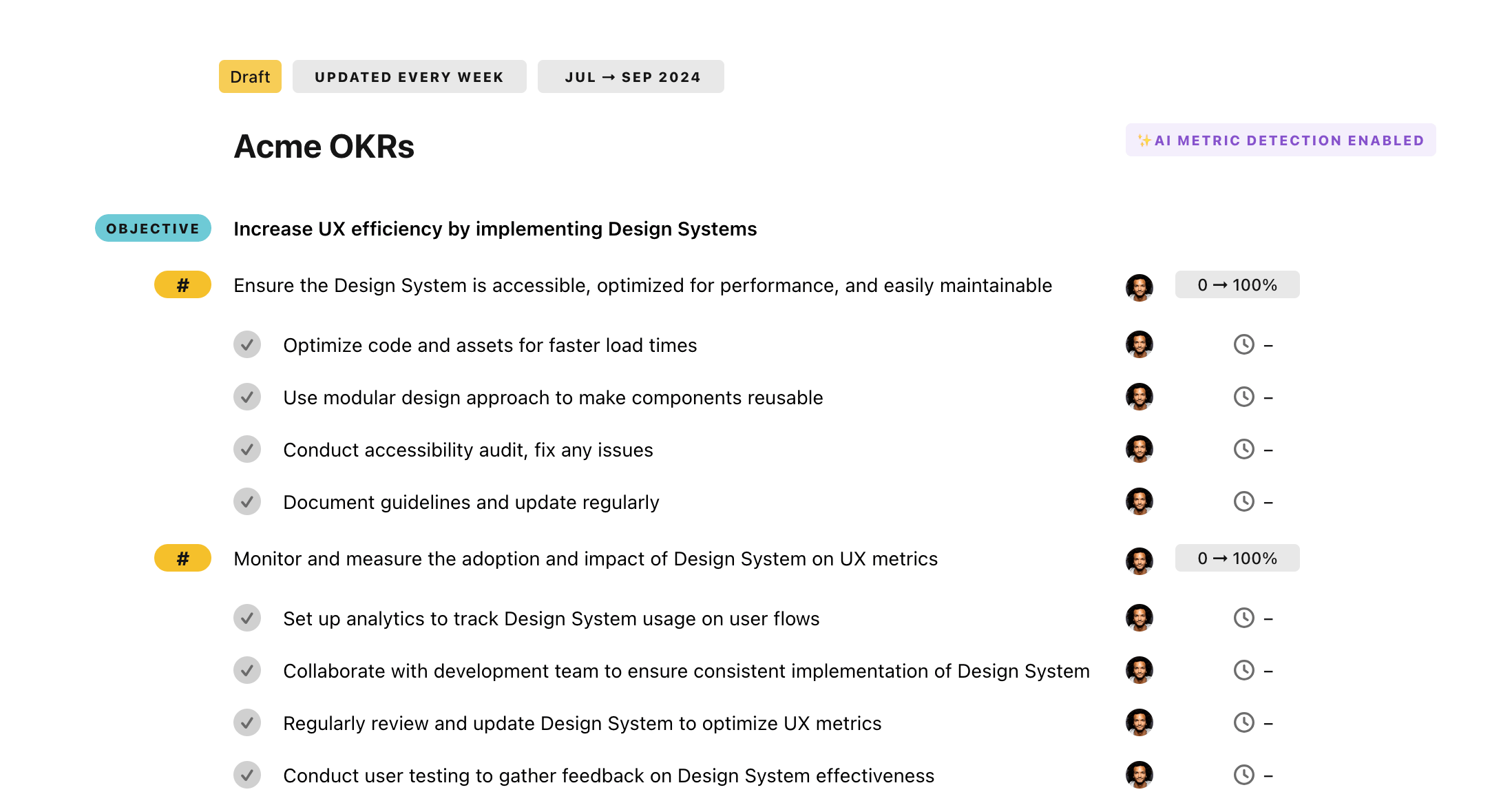
Once your example is in the plan editor, you will be able to:
- Edit the objectives, key results, and tasks
- Click on the target 0 → 100% to set better target
- Use the tips and the AI to refine your goals
Step 4. Publish your plan
Once you’re done editing, you can publish your plan to switch to the goal-tracking mode.
From there you will have access to all the features that will help you and your team save hours with OKR reporting.
- 10+ built-in dashboards to visualise progress on your goals
- Weekly reminders, data connectors, and smart notifications
- 9 views to map OKRs to strategic projects
- Strategy map to align teams at scale