15 customisable OKR examples for Security Team
What are Security Team OKRs?
The Objective and Key Results (OKR) framework is a simple goal-setting methodology that was introduced at Intel by Andy Grove in the 70s. It became popular after John Doerr introduced it to Google in the 90s, and it's now used by teams of all sizes to set and track ambitious goals at scale.
Writing good OKRs can be hard, especially if it's your first time doing it. You'll need to center the focus of your plans around outcomes instead of projects.
We understand that setting OKRs can be challenging, so we have prepared a set of examples tailored for Security Team. Take a peek at the templates below to find inspiration and kickstart your goal-setting process.
If you want to learn more about the framework, you can read our OKR guide online.
Building your own Security Team OKRs with AI
While we have some examples available, it's likely that you'll have specific scenarios that aren't covered here. You can use our free AI generator below or our more complete goal-setting system to generate your own OKRs.
Feel free to explore our tools:
- Use our free OKR generator
- Use Tability, a complete platform to set and track OKRs and initiatives, including a GPT-4 powered goal generator
Our customisable Security Team OKRs examples
You will find in the next section many different Security Team Objectives and Key Results. We've included strategic initiatives in our templates to give you a better idea of the different between the key results (how we measure progress), and the initiatives (what we do to achieve the results).
Hope you'll find this helpful!
1. OKRs to upgrade security monitoring team skills and tools
Upgrade security monitoring team skills and tools
Decrease incident response time by 15%
Implement efficient incident detection tools
Train teams on rapid incident response protocols
Schedule regular response time audits
Implement advanced security training for 85% of the team
Identify members who need advanced security training
Source experts for advanced security training
Schedule and coordinate training sessions
Increase the detection rate of suspicious activities by 25%
Train employees on identifying potential suspicious activities
Regularly update and enhance security protocols
Implement advanced analytics tools for better suspicious activity detection
2. OKRs to ensure information security solution meets large customer requirements
Ensure information security solution meets large customer requirements
Adjust our existing information security solution to match found requirements 100%
Develop and implement changes to fill identified gaps
Identify gaps in the current information security solution
Test and fine-tune the updated security solution
Identify and understand the requirements of 10 major customers by consulting directly
Schedule one-on-one meetings with each of the 10 major customers
Review and analyze all customer feedback to understand requirements
Prepare specific, clear questions for customer consultation
Successfully pass 10 customer audits confirming solution's compliance with their requirements
Review and understand all customer's requirements for each solution
Conduct internal audits to ensure compliance with requirements
Collect and organize evidence of compliance for audits
3. OKRs to secure local channels and gain market insights
Secure local channels and gain market insights
Conduct regular market research to gather local market data and information
Conduct surveys or interviews to gather insights and preferences of local customers
Identify key competitors and their market share in the local market
Monitor industry trends and analyze data to identify emerging opportunities in the local market
Establish partnerships with local stakeholders to enhance channel security
Collaborate with stakeholders to develop and implement strategies for enhancing channel security
Identify key local stakeholders with expertise in channel security
Initiate meetings with stakeholders to discuss potential partnership opportunities
Increase security measures on local channels to reduce unauthorized access
Implement two-factor authentication for all user accounts on local channels
Conduct regular security audits and penetration testing on local channels to identify and resolve vulnerabilities
Regularly update and patch software on local channels to address security vulnerabilities
Implement data analytics tools to analyze market trends and consumer behavior
Train and educate the team on how to effectively use the selected data analytics tools
Research and compare various data analytics tools available in the market
Determine key metrics and indicators to track market trends and consumer behavior
4. OKRs to improve website security through effective deployment of content security policy
Improve website security through effective deployment of content security policy
Reduce the number of security breaches and incidents related to content vulnerabilities
Develop and implement comprehensive content security policies and guidelines
Regularly update and patch content management systems and software to mitigate security risks
Provide ongoing training and awareness programs to educate employees about content vulnerabilities
Conduct regular security audits to identify and address content vulnerabilities
Increase overall security rating of the website as measured by independent security auditing tools
Implement SSL/TLS certificates to enable secure HTTPS communication for the website
Conduct penetration tests to identify and fix potential weak points in the website's security
Implement strong and unique passwords, two-factor authentication, and regular user access reviews
Regularly update and patch all software and plugins to address known vulnerabilities
Implement and activate content security policy across all website pages
Define and document the content security policy guidelines and restrictions
Conduct a thorough website audit to identify potential security vulnerabilities
Test and validate the implemented content security policy for effectiveness and accuracy
Modify website code to include the content security policy header on all pages
Enhance user experience by minimizing false positive alerts from the content security policy
Implement machine learning algorithms to optimize content security policy detection
Analyze log data to identify patterns and fine-tune alert triggers
Review and update content security policy rules for better accuracy
Collaborate with developers to eliminate false positives through code improvements
5. OKRs to bolster Protection Against P1 Issues
Bolster Protection Against P1 Issues
Improve first-time resolution rate for P1 issues to 70% across all teams
Train agents on P1 issue recognition and resolution
Implement P1 issue escalation protocol
Regularly review P1 resolution analytics
Implement a 25% reduction in P1 issues through improved security protocols
Train staff in improved security protocols
Identify vulnerabilities in current security protocols
Develop improved, stringent security measures
Achieve 90% staff training completion on new security measures by quarter end
Monitor and report staff training progress regularly
Schedule mandatory training sessions for all staff
Develop comprehensive security training program
6. OKRs to implement and maintain SOCII compliance measures
Ensure ongoing SOCII compliance
Conduct regular testing and auditing to assess SOCII compliance status
Train and educate all relevant teams on SOCII compliance regulations and best practices
Monitor and promptly address any SOCII compliance gaps or violations identified
Establish a dedicated team to promptly address and resolve any identified SOCII compliance issues
Implement corrective measures to address identified SOCII compliance gaps promptly
Conduct regular audits to identify any SOCII compliance gaps or violations
Maintain a vigilant monitoring system to detect any new SOCII compliance violations
Implement and maintain necessary controls and processes to meet SOCII requirements
Conduct initial assessment of current controls and processes to identify gaps
Develop and document new controls and processes to fulfill SOCII requirements
Regularly monitor and evaluate controls and processes to ensure ongoing compliance
Train and educate employees on the importance and execution of SOCII controls
7. OKRs to achieve ISO 27001 certification with an action plan
Achieve ISO 27001 certification with an action plan
Develop and implement necessary policies and procedures to align with ISO 27001 standards
Develop new policies and procedures to meet ISO 27001 standards
Communicate and train employees on the new policies and procedures
Conduct a gap analysis to identify policy and procedure gaps
Regularly review and update policies and procedures to ensure compliance with ISO 27001
Conduct a comprehensive gap analysis to identify all compliance requirements
Successfully pass the external ISO 27001 certification audit conducted by a certified auditor
Update and document all necessary processes and procedures in accordance with ISO 27001
Conduct a comprehensive review of the ISO 27001 standard requirements and guidelines
Implement a risk management framework aligned with the ISO 27001 requirements
Train employees on ISO 27001 procedures and their roles in maintaining compliance
Train all employees on information security awareness and best practices
8. OKRs to strengthen network security through enhanced logging capabilities
Strengthen network security through enhanced logging capabilities
Implement centralized logging infrastructure to capture and store network activity data
Regularly monitor and maintain the centralized logging infrastructure to ensure uninterrupted data capture
Assess existing network infrastructure to identify suitable centralized logging solutions
Configure the centralized logging infrastructure to collect and store the network activity data
Determine the appropriate tools and technologies required for capturing network activity data
Increase network security by configuring an intrusion detection system (IDS) with real-time monitoring capabilities
Improve incident response effectiveness by integrating logging data with a security information and event management (SIEM) system
Regularly review and fine-tune the integration and alerting processes to optimize incident response
Analyze current logging data sources and identify gaps for integration with the SIEM system
Develop standardized alerting rules within the SIEM system based on integrated logging data
Configure the SIEM system to ingest and aggregate logging data from all relevant sources
Identify and resolve security vulnerabilities by regularly reviewing and analyzing network log data
Set up a regular schedule for reviewing and analyzing network log data
Generate reports based on network log data analysis to prioritize and address vulnerabilities
Implement necessary measures to resolve identified security vulnerabilities promptly and effectively
Use security software to identify and monitor potential security vulnerabilities
9. OKRs to enhance application security knowledge and awareness among teams
Improve application security knowledge and awareness
Increase the frequency of security checklist reviews by 50%
Conduct at least one security training session per team
Provide secure coding guidelines and best practices to each team
Implement a mandatory security certification program for all teams
10. OKRs to successfully complete annual security training
Successfully complete annual security training
Apply learned procedures in simulated security scenarios with zero errors
Practice procedures until executed flawlessly
Review and memorize security procedures thoroughly
Engage in regular simulated security situations
Achieve a minimum of 85% score in end-of-training examination
Seek instructor feedback and clarification when needed
Review all training materials and take detailed notes
Complete daily self-assessments to track progress
Complete 100% of allocated course modules by end of quarter
Reserve dedicated study hours every day
Monitor progress regularly against targets
Set a weekly target for completing course modules
11. OKRs to minimize customer fraud risk exposure
Minimize customer fraud risk exposure
Train 90% staff on anti-fraud techniques and identification
Identify relevant anti-fraud training programs or courses
Organize and schedule mandatory training sessions for staff
Monitor and document staff participation and comprehension
Decrease successful fraud cases by 30% through improved system security
Educate employees on recognizing potential fraud
Regularly update and patch security software
Implement advanced fraud detection software systems
Implement new risk-assessment tool improving detection by 20%
Research and select a new risk-assessment tool
Monitor and evaluate tool’s effectiveness
Train team on how to use new tool
12. OKRs to upgrade and streamline physical security operations
Upgrade and streamline physical security operations
Increase security coverage by 20% through additional surveillance systems
Investigate current surveillance system capabilities and limitations
Implement new surveillance systems accordingly
Research and identify potential additional surveillance technology
Decrease response times to security incidents by 25%
Implement a digital security management system with 100% staff training completion
Track and achieve 100% training completion
Choose a comprehensive digital security management system
Develop an all-staff training curriculum for the system
13. OKRs to effective implementation of DevSecOps in the team
Effective implementation of DevSecOps in the team
Achieve zero high-risk vulnerabilities in new software releases for the quarter
Conduct regular, comprehensive vulnerability assessments
Implement stringent security protocols during software development
Ensure timely patching and updates post-release
Train 90% of the team on DevSecOps principles and best practices
Schedule training sessions for each team member
Identify suitable DevSecOps training programs for the team
Monitor progress and ensure completion for 90% of the team
Incorporate automated security checks into 100% of coding pipelines
Integrate selected automated security checks into all coding pipelines
Identify potential automated security solutions available for coding pipelines
Regularly update and maintain the implemented security checks
14. OKRs to attain ISO 27001 certification
Achieve ISO 27001 certification
Implement necessary controls and measures to address identified risks and improve information security
Regularly monitor and test the effectiveness of implemented controls and measures
Establish strong access controls and authentication mechanisms to protect sensitive information
Conduct a comprehensive risk assessment to identify vulnerabilities and potential threats
Develop and implement security policies and procedures based on the identified risks
Train all employees on information security policies and procedures to ensure compliance
Develop a comprehensive training program on information security policies and procedures
Conduct mandatory training sessions for all employees on information security policies and procedures
Provide all employees with updated written materials outlining information security policies and procedures
Regularly assess and evaluate employees' understanding of information security policies and procedures
Conduct a comprehensive risk assessment to identify gaps in information security practices
Develop action plans to address and close the identified gaps in information security practices
Identify potential vulnerabilities and weaknesses in the existing information security infrastructure
Review current information security practices and policies
Assess the potential impact of identified risks on the organization's information and data
Successfully pass the ISO 27001 certification audit conducted by an accredited external body
Address any identified gaps or weaknesses in the information security controls
Prepare and organize all required documentation and evidence for the audit process
Implement necessary improvements to align with ISO 27001 requirements and best practices
Conduct a thorough internal review of all information security controls and processes
15. OKRs to implement cutting-edge bot detection technologies for website data
Implement cutting-edge bot detection technologies for website data
Achieve 95% accuracy rate in detecting bots using newly implemented technologies
Continuously refine and update the models deployed
Test algorithms with diverse sets of data
Implement new machine learning algorithms for bot detection
Integrate and test 3 selected bot detection technologies on our website
Choose three suitable bot detection technologies for our website
Conduct thorough testing to ensure effectiveness
Implement these technologies into our site's backend
Identify and study 10 new bot detection methods from industry research
Analyze each method's pros, cons, and applicability
Select 10 recent industry research on bot detection methods
Prepare a report summarizing findings
Security Team OKR best practices to boost success
Generally speaking, your objectives should be ambitious yet achievable, and your key results should be measurable and time-bound (using the SMART framework can be helpful). It is also recommended to list strategic initiatives under your key results, as it'll help you avoid the common mistake of listing projects in your KRs.
Here are a couple of best practices extracted from our OKR implementation guide 👇
Tip #1: Limit the number of key results
The #1 role of OKRs is to help you and your team focus on what really matters. Business-as-usual activities will still be happening, but you do not need to track your entire roadmap in the OKRs.
We recommend having 3-4 objectives, and 3-4 key results per objective. A platform like Tability can run audits on your data to help you identify the plans that have too many goals.
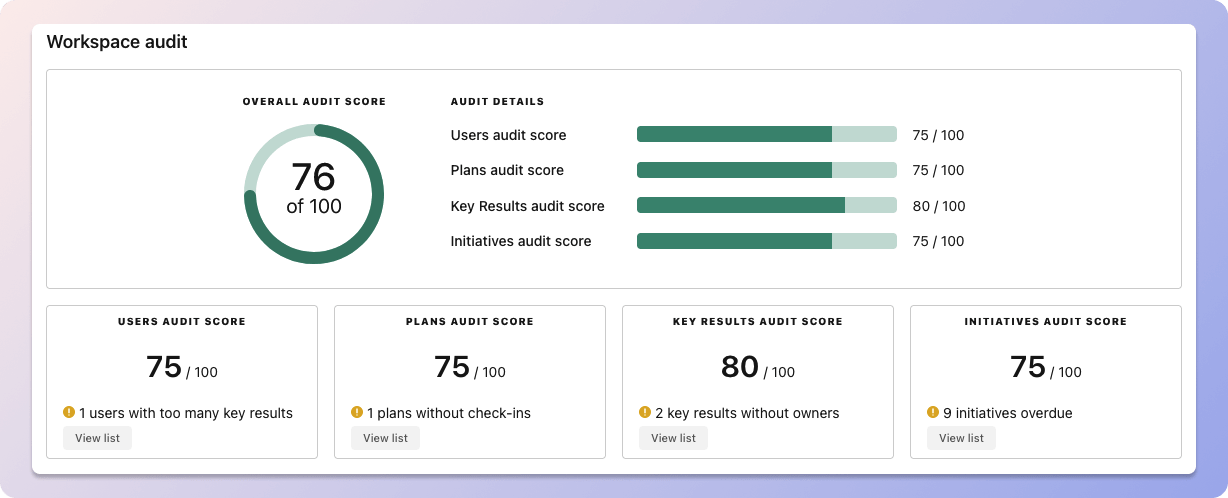 Tability's audit dashboard will highlight opportunities to improve OKRs
Tability's audit dashboard will highlight opportunities to improve OKRsTip #2: Commit to weekly OKR check-ins
Don't fall into the set-and-forget trap. It is important to adopt a weekly check-in process to get the full value of your OKRs and make your strategy agile – otherwise this is nothing more than a reporting exercise.
Being able to see trends for your key results will also keep yourself honest.
 Tability's check-ins will save you hours and increase transparency
Tability's check-ins will save you hours and increase transparencyTip #3: No more than 2 yellow statuses in a row
Yes, this is another tip for goal-tracking instead of goal-setting (but you'll get plenty of OKR examples above). But, once you have your goals defined, it will be your ability to keep the right sense of urgency that will make the difference.
As a rule of thumb, it's best to avoid having more than 2 yellow/at risk statuses in a row.
Make a call on the 3rd update. You should be either back on track, or off track. This sounds harsh but it's the best way to signal risks early enough to fix things.
How to turn your Security Team OKRs in a strategy map
The rules of OKRs are simple. Quarterly OKRs should be tracked weekly, and yearly OKRs should be tracked monthly. Reviewing progress periodically has several advantages:
- It brings the goals back to the top of the mind
- It will highlight poorly set OKRs
- It will surface execution risks
- It improves transparency and accountability
Spreadsheets are enough to get started. Then, once you need to scale you can use a proper OKR platform to make things easier.
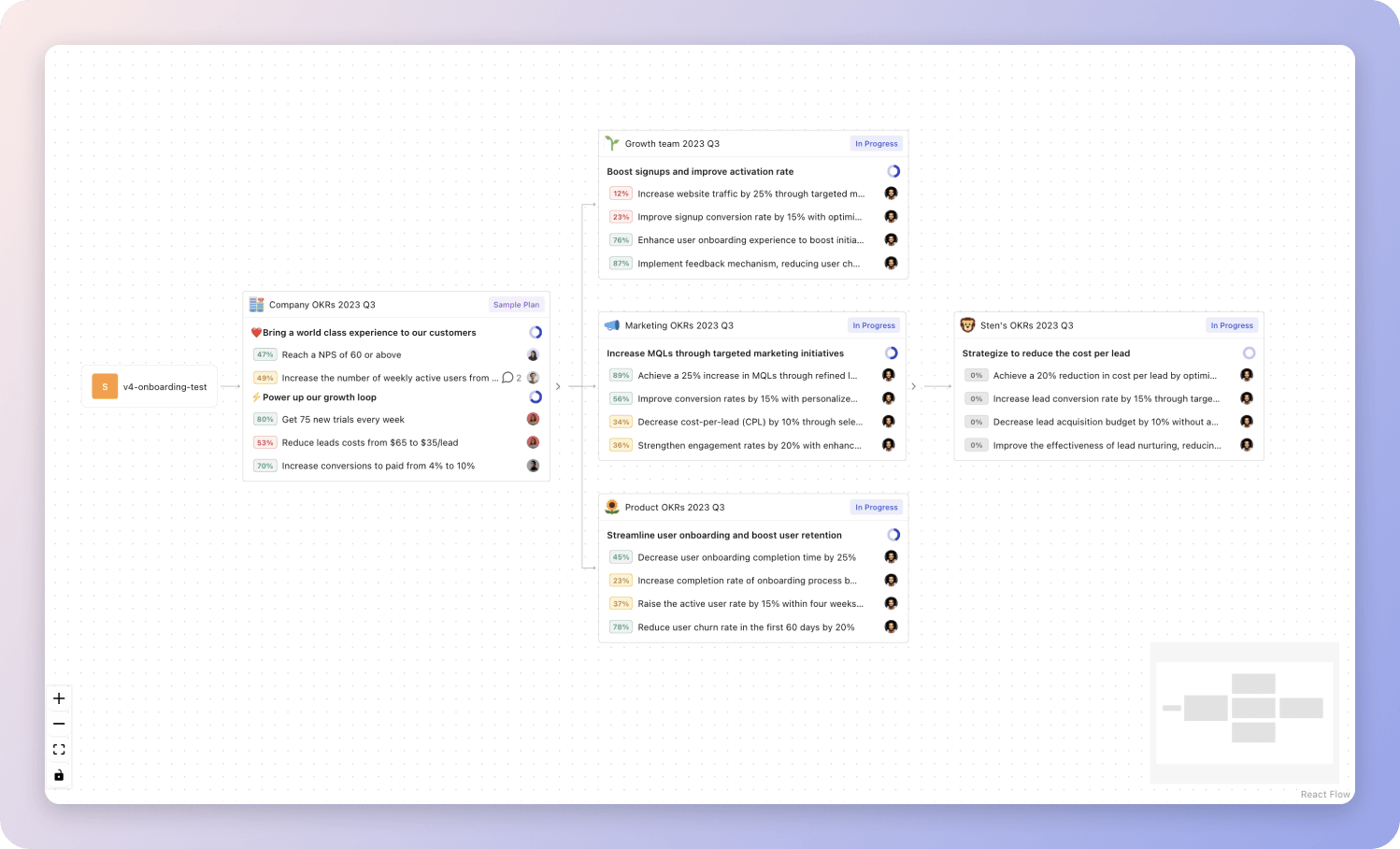 Tability's Strategy Map makes it easy to see all your org's OKRs
Tability's Strategy Map makes it easy to see all your org's OKRsIf you're not yet set on a tool, you can check out the 5 best OKR tracking templates guide to find the best way to monitor progress during the quarter.
More Security Team OKR templates
We have more templates to help you draft your team goals and OKRs.
OKRs to boost academic rigor for improved college readiness
OKRs to improve team productivity and efficiency
OKRs to implement strategies to decrease recovery time
OKRs to significantly increase MICE revenue and diversify client portfolio
OKRs to achieve production readiness for MassBalancer ISCC EU feature
OKRs to implement successful project tracking and KPI definition system
OKRs resources
Here are a list of resources to help you adopt the Objectives and Key Results framework.
- To learn: What is the meaning of OKRs
- Blog posts: ODT Blog
- Success metrics: KPIs examples
Create more examples in our app
You can use Tability to create OKRs with AI – and keep yourself accountable 👀
Tability is a unique goal-tracking platform built to save hours at work and help teams stay on top of their goals.
 1 Create your workspace
1 Create your workspace 2 Build plans in seconds with AI
2 Build plans in seconds with AI 3Track your progress
3Track your progress