Tability is a cheatcode for goal-driven teams. Set perfect OKRs with AI, stay focused on the work that matters.
What are Incident Response OKRs?
The OKR acronym stands for Objectives and Key Results. It's a goal-setting framework that was introduced at Intel by Andy Grove in the 70s, and it became popular after John Doerr introduced it to Google in the 90s. OKRs helps teams has a shared language to set ambitious goals and track progress towards them.
Formulating strong OKRs can be a complex endeavor, particularly for first-timers. Prioritizing outcomes over projects is crucial when developing your plans.
We've tailored a list of OKRs examples for Incident Response to help you. You can look at any of the templates below to get some inspiration for your own goals.
If you want to learn more about the framework, you can read our OKR guide online.
The best tools for writing perfect Incident Response OKRs
Here are 2 tools that can help you draft your OKRs in no time.
Tability AI: to generate OKRs based on a prompt
Tability AI allows you to describe your goals in a prompt, and generate a fully editable OKR template in seconds.
- 1. Create a Tability account
- 2. Click on the Generate goals using AI
- 3. Describe your goals in a prompt
- 4. Get your fully editable OKR template
- 5. Publish to start tracking progress and get automated OKR dashboards
Watch the video below to see it in action 👇
Tability Feedback: to improve existing OKRs
You can use Tability's AI feedback to improve your OKRs if you already have existing goals.
- 1. Create your Tability account
- 2. Add your existing OKRs (you can import them from a spreadsheet)
- 3. Click on Generate analysis
- 4. Review the suggestions and decide to accept or dismiss them
- 5. Publish to start tracking progress and get automated OKR dashboards
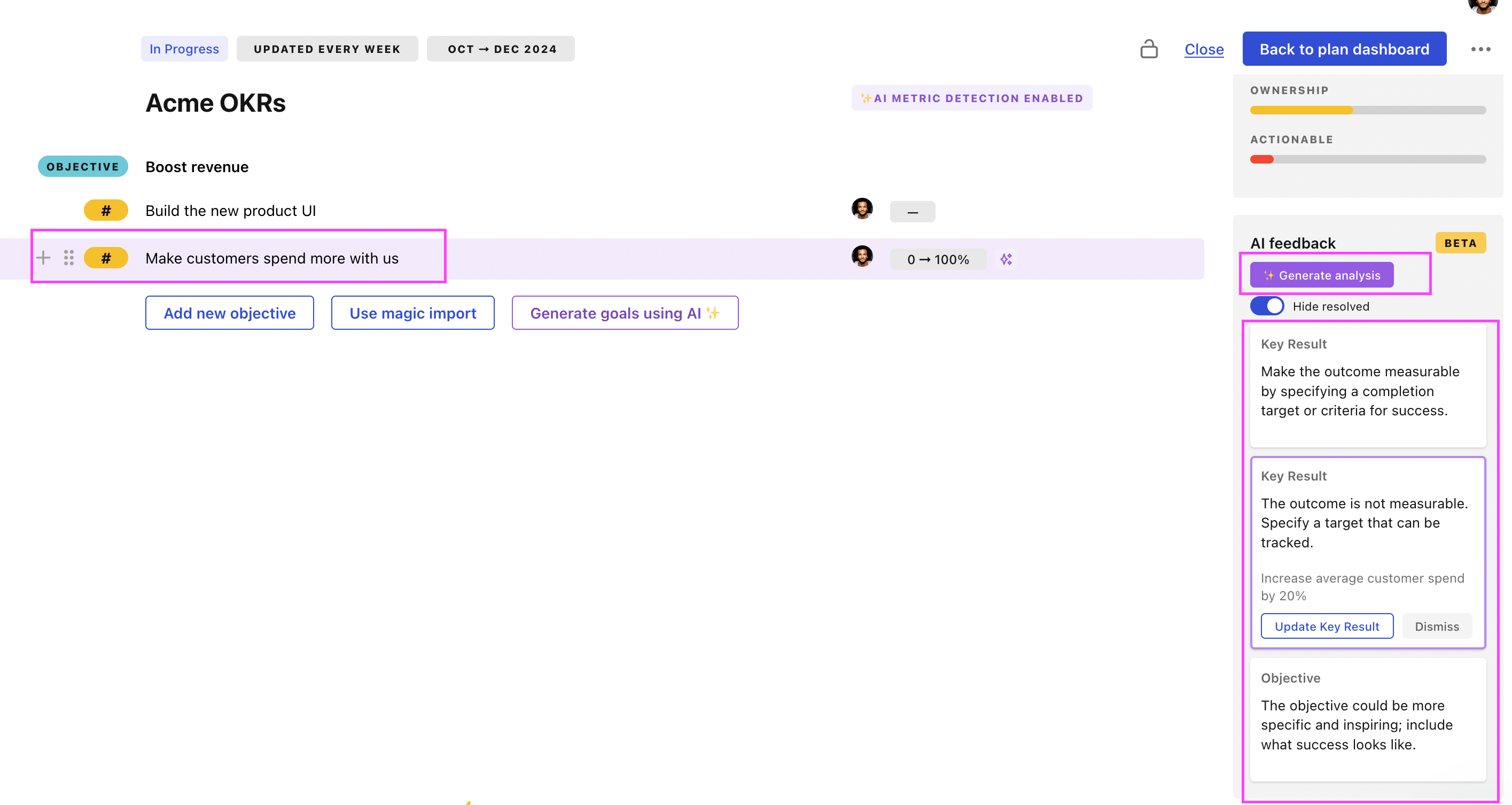
Tability will scan your OKRs and offer different suggestions to improve them. This can range from a small rewrite of a statement to make it clearer to a complete rewrite of the entire OKR.
Incident Response OKRs examples
You'll find below a list of Objectives and Key Results templates for Incident Response. We also included strategic projects for each template to make it easier to understand the difference between key results and projects.
Hope you'll find this helpful!
OKRs to enhance incident response efficiency
ObjectiveEnhance incident response efficiency
KRImprove incident tracking software to accelerate case-handling efficiency by 20%
Implement automated workflows in incident tracking software
Enhance software to prioritize incidents based on severity
Train employees to efficiently use updated software
KRImplement automated incident alert system increasing notification speed by 35%
Train employees on system usage
Install and configure selected alert system
Research most efficient automated incident alert systems
KRProvide specialized response training to staff improving processing time by 25%
Identify personnel needing specialized response training
Create or outsource effective, specific training modules
Implement training sessions and track improvements
OKRs to improve efficiency of incident response
ObjectiveImprove efficiency of incident response
KRDecrease median incident respond time by 30%
Enhance team training on rapid response protocols
Implement a prioritization system for assessing incidents
Invest in automated incident handling tools
KRImplement new training to decrease initial reaction time by 20%
Identify current weak points in reaction time training
Collaborate with experts to develop effective training methods
Introduce new training program to staff
KRIncrease the resolution rate of first responses by 25%
Update and upgrade customer service software tools
Review and refine existing support protocols
Implement ongoing training programs for customer service representatives
OKRs to improve and Optimize Incident Response
ObjectiveImprove and Optimize Incident Response
KRIncrease incident response speed by 30% to reduce downtime
Implement automated incident detection software
Train staff on efficient response protocols
Develop a streamlined incident escalation process
KRTrain all team members on incident response protocols and breach simulations
Simulate potential breach scenarios for practice
Organize incident response protocol training for all team members
Follow-up with tests to assess team's knowledge and readiness
KRImplement at least two innovative incident management tools for better response
Train staff on usage and implementation of tools
Choose two tools that best suit our needs
Research latest innovative incident management tools
OKRs to enhance SOC SIEM monitoring tools for efficient detection and response
ObjectiveEnhance SOC SIEM monitoring tools for efficient detection and response
KRDecrease response time by 30% by integrating automation into incident response workflows
Identify routine tasks in incident response workflows
Test and refine the automated systems
Implement automation solutions for identified tasks
KRConduct two test scenarios per month to ensure an upgrade in overall system efficiency
Execute two test scenarios regularly
Analyze and document test results for improvements
Identify potential scenarios for system testing
KRIncrease detection accuracy by 20% employing machine learning algorithms to SOC SIEM tools
Test and fine-tune ML algorithms to increase accuracy
Integrate these models with existing SOC SIEM tools
Develop advanced machine learning models for better anomaly detection
OKRs to establish the Ethio Cyber Incident Response Team website
ObjectiveEstablish the Ethio Cyber Incident Response Team website
KRComplete documentation of website functionalities and user interface by 50%
Write detailed explanations for half of identified elements
Review, correct and finalize first half of documentation
Identify key functionalities and user interface elements to document
KRSecure digital assets, ensuring 100% website safety and reliability
Regularly update and back-up website systems and data
Implement strong password policies and two-factor authentication
Invest in comprehensive cyber security software
KRAchieve 75% completion of website development and testing
Implement desired features and essential functions
Finalize and optimize website code structure
Conduct thorough functionality and stress testing
OKRs to streamline incident response process to reduce time by 15%
ObjectiveStreamline incident response process to reduce time by 15%
KRDecrease resolution time by 10% through systematic problem-solving methods
Establish a dedicated troubleshooting team
Implement training on efficient problem-solving strategies
Introduce problem-tracking and management software
KRImplement a new incident management system improving efficiency by 10%
Evaluate current incident management process and identify inefficiencies
Research and select a new incident management system
Train staff on new system's usage and procedures
KRTrain team on quick, effective incident identification within 5% fewer hours
Schedule short, focused training sessions for the team
Implement practice drills for faster comprehension
Develop a streamlined incident identification training curriculum
OKRs to enhance incident identification and reporting for better operational transparency
ObjectiveEnhance incident identification and reporting for better operational transparency
KRDeliver bi-weekly operational transparency reports to stakeholders, reflecting a decrease in incidents by 20%
KRImplement a comprehensive incident identification system that reduces unidentified incidents by 25%
Train staff on utilizing and updating the new system
Develop protocol for swift incident identification and response
Track and analyze system effectiveness regularly
KRDevelop a user-friendly reporting process leading to a 30% increase in incident reports
Design an intuitive, straightforward incident reporting form
Develop a responsive helpdesk for immediate assistance
Conduct training on reporting procedures and new system
OKRs to improve Security Operation Centre Incident Response
ObjectiveImprove Security Operation Centre Incident Response
KRReduce average incident response time by 15%
Deploy automated incident detection and response tools
Train team on efficient incident management practices
Regularly conduct response time drills
KRIncrease team's cyber security certification levels by 30%
Plan and allocate budget for necessary certification exams and trainings
Identify current cybersecurity certification levels of all team members
Enroll team in targeted cybersecurity training programs
KRImplement new incident tracking software with 100% team adoption
Train team on new software usage
Evaluate and select suitable incident tracking software
Monitor and ensure full team adoption
OKRs to improve service recovery time in 2024
ObjectiveImprove service recovery time in 2024
KRReduce mean time to recovery (MTTR) by 25% in the next product update
Integrate higher-quality failure-detection mechanisms
Implement automated incident response procedures
Develop comprehensive recovery guideline documents
KRTrain support team on new recovery protocols to attain 90% resolution efficiency
Schedule training sessions on new recovery protocols for support team
Set up regular assessments to measure resolution efficiency
Develop practical exercises to ensure understanding of new protocols
KRImplement automated diagnostic tools to decrease escalation incidents by 30%
Identify suitable automated diagnostic tools for system optimization
Train staff on proper usage and implementation of these tools
Purchase and install the selected automated diagnostic tools
OKRs to improve the reliability and efficiency of IT Infrastructure
ObjectiveImprove the reliability and efficiency of IT Infrastructure
KRDecrease system downtime by 30% through proactive maintenance and upgrades
Develop a regular schedule for proactive maintenance and system check-ups
Implement latest upgrades and patches in a timely manner
Monitor system metrics regularly to spot potential failures
KRImprove incident response time by 20% for high-severity issues
Simplify processes for faster issue resolution
Train staff on efficient incident response protocol
Implement an alert system for high-severity issues
KRImplement a new automation system reducing manual tasks by 25%
Train employees on new automation system usage
Select appropriate automation software or tool
Identify processes suitable for automation within the company
Incident Response OKR best practices
Generally speaking, your objectives should be ambitious yet achievable, and your key results should be measurable and time-bound (using the SMART framework can be helpful). It is also recommended to list strategic initiatives under your key results, as it'll help you avoid the common mistake of listing projects in your KRs.
Here are a couple of best practices extracted from our OKR implementation guide 👇
Tip #1: Limit the number of key results
Having too many OKRs is the #1 mistake that teams make when adopting the framework. The problem with tracking too many competing goals is that it will be hard for your team to know what really matters.
We recommend having 3-4 objectives, and 3-4 key results per objective. A platform like Tability can run audits on your data to help you identify the plans that have too many goals.
Tip #2: Commit to weekly OKR check-ins
Setting good goals can be challenging, but without regular check-ins, your team will struggle to make progress. We recommend that you track your OKRs weekly to get the full benefits from the framework.
Being able to see trends for your key results will also keep yourself honest.
Tip #3: No more than 2 yellow statuses in a row
Yes, this is another tip for goal-tracking instead of goal-setting (but you'll get plenty of OKR examples above). But, once you have your goals defined, it will be your ability to keep the right sense of urgency that will make the difference.
As a rule of thumb, it's best to avoid having more than 2 yellow/at risk statuses in a row.
Make a call on the 3rd update. You should be either back on track, or off track. This sounds harsh but it's the best way to signal risks early enough to fix things.
Save hours with automated Incident Response OKR dashboards
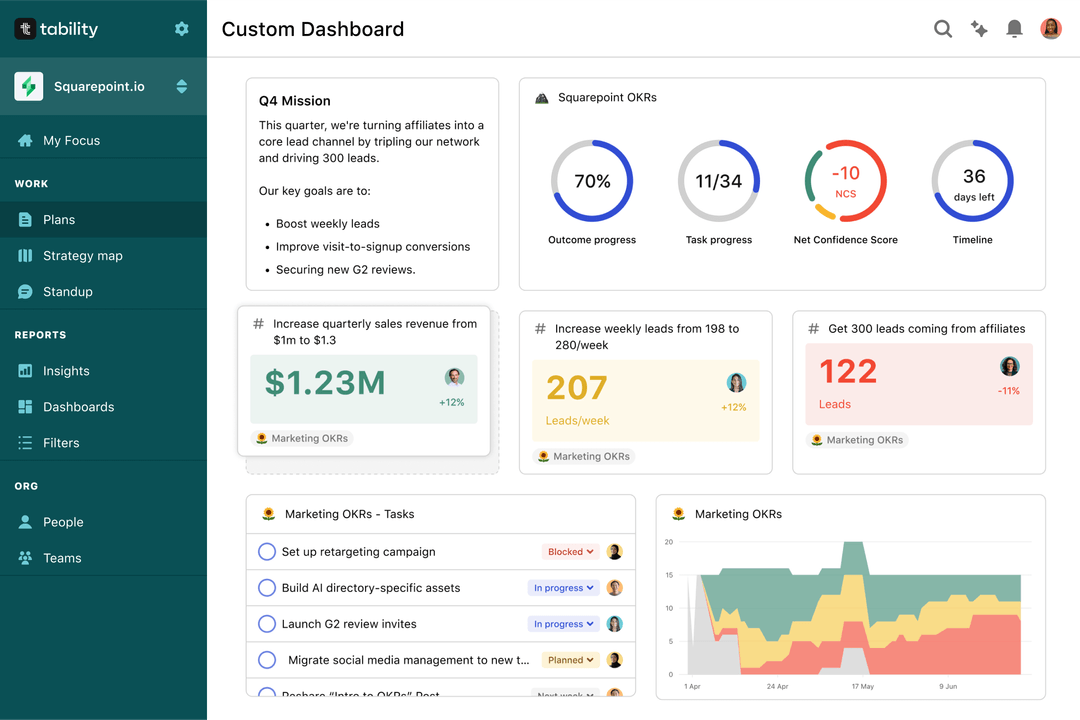
OKRs without regular progress updates are just KPIs. You'll need to update progress on your OKRs every week to get the full benefits from the framework. Reviewing progress periodically has several advantages:
- It brings the goals back to the top of the mind
- It will highlight poorly set OKRs
- It will surface execution risks
- It improves transparency and accountability
Most teams should start with a spreadsheet if they're using OKRs for the first time. Then, you can move to Tability to save time with automated OKR dashboards, data connectors, and actionable insights.
How to get Tability dashboards:
- 1. Create a Tability account
- 2. Use the importers to add your OKRs (works with any spreadsheet or doc)
- 3. Publish your OKR plan
That's it! Tability will instantly get access to 10+ dashboards to monitor progress, visualise trends, and identify risks early.
More Incident Response OKR templates
We have more templates to help you draft your team goals and OKRs.
OKRs to determine the business benefits of SAP S4
OKRs to enhance website visibility and conversion rate
OKRs to successfully orchestrate an engaging food street event
OKRs to successfully support the launch of Unified GA
OKRs to improve the quality and relevancy of content through comprehensive revisions
OKRs to publish an engaging Android app and acquire monthly subscribers