8 customisable OKR examples for Cybersecurity Training
What are Cybersecurity Training OKRs?
The Objective and Key Results (OKR) framework is a simple goal-setting methodology that was introduced at Intel by Andy Grove in the 70s. It became popular after John Doerr introduced it to Google in the 90s, and it's now used by teams of all sizes to set and track ambitious goals at scale.
Creating impactful OKRs can be a daunting task, especially for newcomers. Shifting your focus from projects to outcomes is key to successful planning.
We have curated a selection of OKR examples specifically for Cybersecurity Training to assist you. Feel free to explore the templates below for inspiration in setting your own goals.
If you want to learn more about the framework, you can read our OKR guide online.
Building your own Cybersecurity Training OKRs with AI
While we have some examples available, it's likely that you'll have specific scenarios that aren't covered here. You can use our free AI generator below or our more complete goal-setting system to generate your own OKRs.
Feel free to explore our tools:
- Use our free OKR generator
- Use Tability, a complete platform to set and track OKRs and initiatives, including a GPT-4 powered goal generator
Our customisable Cybersecurity Training OKRs examples
We've added many examples of Cybersecurity Training Objectives and Key Results, but we did not stop there. Understanding the difference between OKRs and projects is important, so we also added examples of strategic initiatives that relate to the OKRs.
Hope you'll find this helpful!
1. OKRs to enhance fraud detection and prevention in the payment system
Enhance fraud detection and prevention in the payment system
Reduce the number of fraudulent transactions by 25% through enhanced system security
Invest in fraud detection and prevention software
Conduct regular cybersecurity audits and fixes
Implement advanced encryption techniques for payment transactions
Implement machine learning algorithms to increase fraud detection accuracy by 40%
Train the algorithms with historical fraud data
Select appropriate machine learning algorithms for fraud detection
Test and tweak models' accuracy to achieve a 40% increase
Train staff on new security protocols to reduce manual errors by 30%
Monitor and evaluate reduction in manual errors post-training
Schedule mandatory training sessions for all staff
Develop comprehensive training on new security protocols
2. OKRs to embed security consciousness in business operations
Embed security consciousness in business operations
Reduce security breaches by 25% through rigorous employee training
Implement mandatory cybersecurity training for all employees
Schedule regular refresher courses on data protection
Update security policies and disseminate to staff
Establish a quarterly security audit to identify potential vulnerabilities
Schedule regular audits with a professional auditor
Define the scope of each quarterly security audit
Create a process to address identified vulnerabilities
Achieve 100% compliance on mandatory security awareness training by all employees
Organize regular training sessions for all personnel
Monitor and document each employee's training progress
Distribute security awareness training materials to all employees
3. OKRs to enhance cybersecurity maturity in the organization
Enhance cybersecurity maturity in the organization
Implement a cybersecurity awareness training program for 85% of the staff
Schedule training sessions with 85% of staff
Track and report staff training completion
Identify suitable cybersecurity training program for staff
Reduce the number of security incidents by 30%
Implement regular, mandatory cybersecurity training sessions
Update all systems and applications routinely
Enable stringent password protocols
Achieve ISO 27001 cybersecurity certification
Prepare and pass the ISO 27001 audit
Implement necessary controls and security measures
Conduct a comprehensive risk assessment of your information security system
4. OKRs to strengthen overall company cybersecurity knowledge and protocol compliance
Strengthen overall company cybersecurity knowledge and protocol compliance
Decrease the occurrence of cybersecurity breaches by 30%
Implement regular, mandatory cybersecurity training for staff
Regularly update security software and firewalls
Conduct routine system vulnerability assessments
Pass cybersecurity compliance audits with a success rate of 95% or more
Consistently monitor and evaluate system vulnerabilities
Regularly train staff on cybersecurity best practices
Implement updated, robust cybersecurity protocols and software
Increase employee participation in cybersecurity training sessions by 25%
Personalize training sessions to individual role requirements
Boost training session visibility through internal communications
Implement incentives for completing cybersecurity training
5. OKRs to enhance security measures to mitigate OTP attacks
Enhance security measures to mitigate OTP attacks
Reduce unauthorized access attempts by 50% through enhanced account lockout mechanisms
Increase employee awareness and adherence to security protocols through regular training sessions
Conduct bi-weekly security training sessions for all employees
Offer incentives or rewards for employees who consistently demonstrate adherence to security protocols
Provide employees with updated written materials outlining security protocols
Utilize interactive training methods, such as quizzes or simulations, to engage employees
Improve OTP delivery and verification mechanisms to ensure prompt and secure delivery
Implement multi-factor authentication for all critical systems and user accounts
Select and implement a reliable and user-friendly multi-factor authentication solution
Regularly monitor and review multi-factor authentication logs and make necessary enhancements
Notify all users of the upcoming implementation and provide necessary training and guidelines
Conduct a thorough inventory of all critical systems and user accounts
6. OKRs to enhance overall Identity and Access Management system
Enhance overall Identity and Access Management system
Increase employee training on access management protocols by 80%
Allocate time for employees to complete training
Implement mandatory participation in training sessions
Develop detailed access management training sessions
Reduce unauthorized access incidents by 50%
Conduct regular cybersecurity awareness training
Implement two-factor authentication for all system users
Regularly audit system access and permissions
Implement Multi-Factor Authentication for all employees by 70%
Migrate 70% of employees across to this new security protocol
Identify all systems requiring enhanced Multi-Factor Authentication security measures
Conduct training sessions on Multi-Factor Authentication usage
7. OKRs to enhance data privacy and cybersecurity measures to safeguard sensitive information
Enhance data privacy and cybersecurity measures to safeguard sensitive information
Implement a comprehensive data encryption system across all relevant platforms
Assess current data encryption measures and identify gaps for improvement
Develop and implement a standardized data encryption protocol for all platforms
Conduct regular audits to ensure consistent adherence to the data encryption system
Train employees on proper data encryption practices and its importance in data security
Conduct regular vulnerability assessments and address identified risks within set timeframes
Quickly prioritize and address identified risks based on severity levels
Schedule regular vulnerability assessments according to established timelines
Establish set timeframes for risk mitigation and ensure timely execution
Develop a clear process for tracking and documenting vulnerability assessment findings
Increase employee awareness and participation in cybersecurity training programs by 25%
Recognize and reward employees who actively participate in cybersecurity training
Create engaging and interactive modules for cybersecurity training programs
Organize lunch and learn sessions to promote employee awareness about cybersecurity threats
Send regular email reminders about upcoming cybersecurity training sessions
Achieve a 10% improvement in overall incident response time, ensuring timely mitigation of potential breaches
Streamline incident response processes and eliminate any unnecessary steps for faster response times
Regularly evaluate and improve incident response plans to enhance efficiency and effectiveness
Provide comprehensive training to all personnel involved in incident response procedures
Implement automation tools to expedite the identification and containment of potential breaches
8. OKRs to enhance the organization's cybersecurity infrastructure
Enhance the organization's cybersecurity infrastructure
Implement multi-factor authentication for all internal systems by the end of Q2
Implement selected multi-factor authentication solution
Assess current authentication methods across all systems
Identify suitable multi-factor authentication solutions
Conduct cybersecurity training programs for 90% of employees
Identify the key cybersecurity principles for training content
Organize training schedules for employees
Evaluate post-training comprehension and application
Carry out system vulnerability assessment every week to spot and fix any gaps
Implement necessary fixes to detected vulnerabilities immediately
Analyze assessment results to identify security gaps
Schedule weekly system vulnerability assessments
Cybersecurity Training OKR best practices to boost success
Generally speaking, your objectives should be ambitious yet achievable, and your key results should be measurable and time-bound (using the SMART framework can be helpful). It is also recommended to list strategic initiatives under your key results, as it'll help you avoid the common mistake of listing projects in your KRs.
Here are a couple of best practices extracted from our OKR implementation guide 👇
Tip #1: Limit the number of key results
Having too many OKRs is the #1 mistake that teams make when adopting the framework. The problem with tracking too many competing goals is that it will be hard for your team to know what really matters.
We recommend having 3-4 objectives, and 3-4 key results per objective. A platform like Tability can run audits on your data to help you identify the plans that have too many goals.
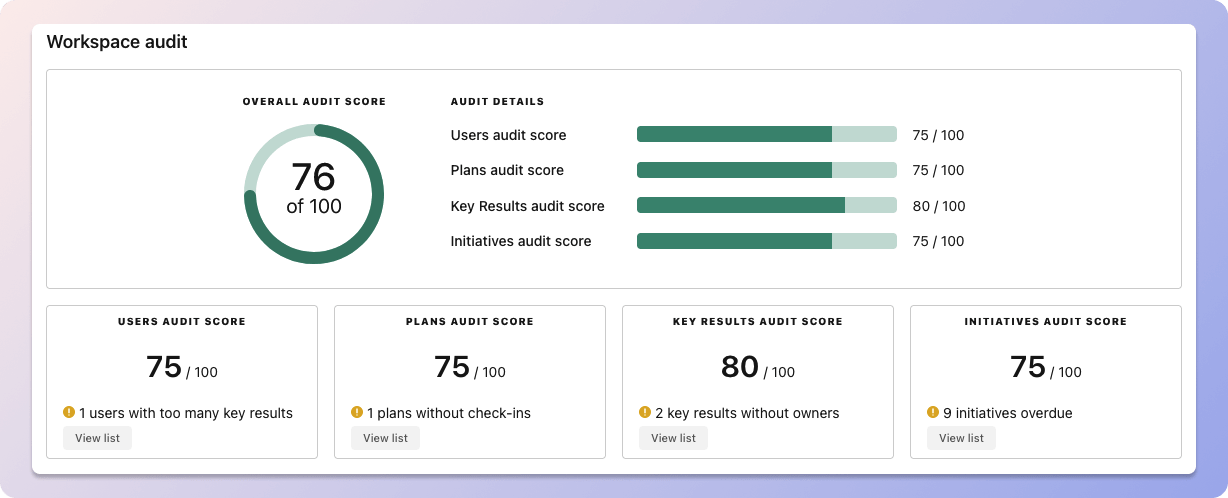 Tability's audit dashboard will highlight opportunities to improve OKRs
Tability's audit dashboard will highlight opportunities to improve OKRsTip #2: Commit to weekly OKR check-ins
Setting good goals can be challenging, but without regular check-ins, your team will struggle to make progress. We recommend that you track your OKRs weekly to get the full benefits from the framework.
Being able to see trends for your key results will also keep yourself honest.
 Tability's check-ins will save you hours and increase transparency
Tability's check-ins will save you hours and increase transparencyTip #3: No more than 2 yellow statuses in a row
Yes, this is another tip for goal-tracking instead of goal-setting (but you'll get plenty of OKR examples above). But, once you have your goals defined, it will be your ability to keep the right sense of urgency that will make the difference.
As a rule of thumb, it's best to avoid having more than 2 yellow/at risk statuses in a row.
Make a call on the 3rd update. You should be either back on track, or off track. This sounds harsh but it's the best way to signal risks early enough to fix things.
How to turn your Cybersecurity Training OKRs in a strategy map
Your quarterly OKRs should be tracked weekly in order to get all the benefits of the OKRs framework. Reviewing progress periodically has several advantages:
- It brings the goals back to the top of the mind
- It will highlight poorly set OKRs
- It will surface execution risks
- It improves transparency and accountability
Most teams should start with a spreadsheet if they're using OKRs for the first time. Then, once you get comfortable you can graduate to a proper OKRs-tracking tool.
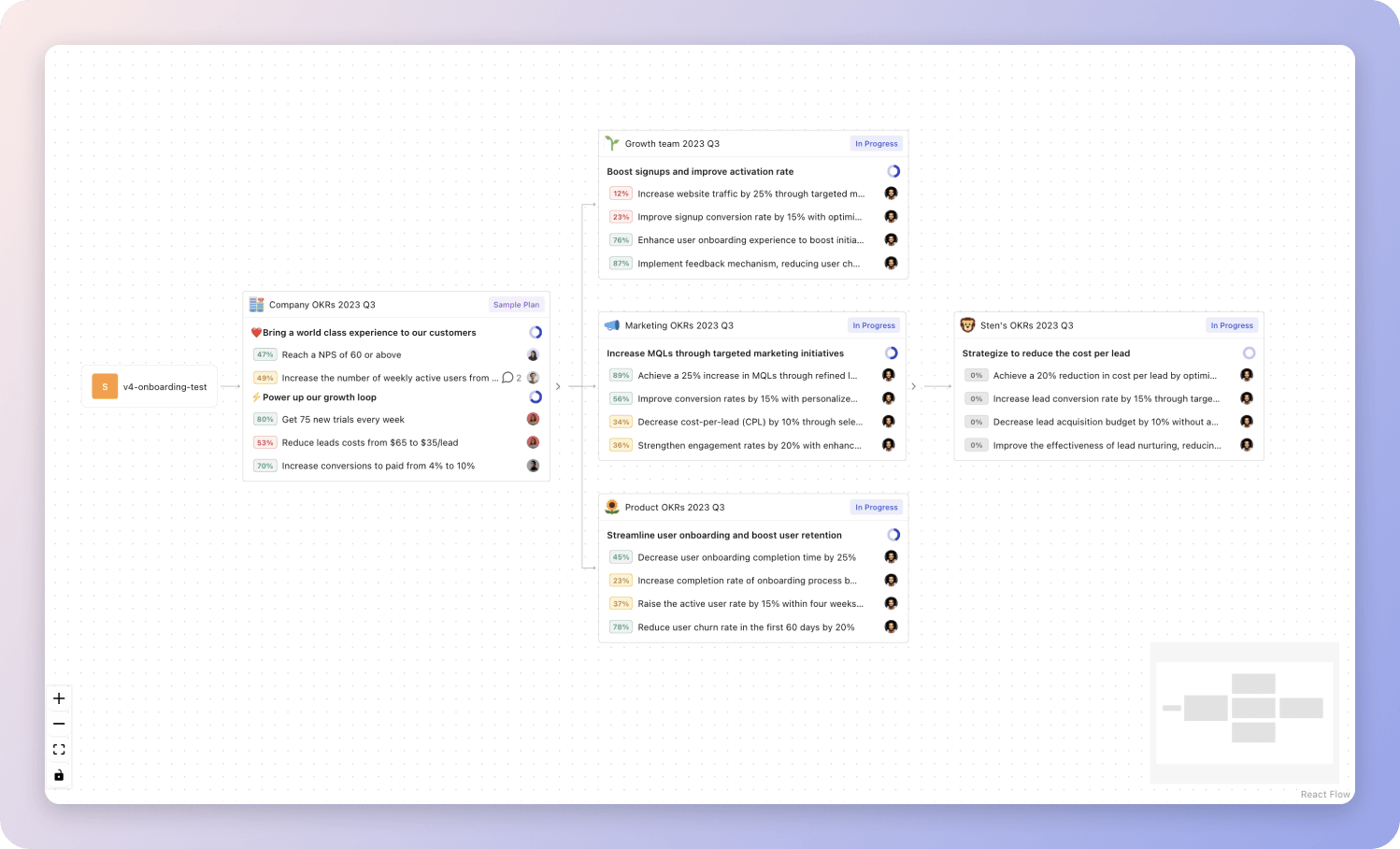 Tability's Strategy Map makes it easy to see all your org's OKRs
Tability's Strategy Map makes it easy to see all your org's OKRsIf you're not yet set on a tool, you can check out the 5 best OKR tracking templates guide to find the best way to monitor progress during the quarter.
More Cybersecurity Training OKR templates
We have more templates to help you draft your team goals and OKRs.
OKRs to amplify our product's feature set
OKRs to foster open communication and continual improvement within the team
OKRs to increase performance opportunities for musicians
OKRs to successfully complete and submit a quality financial report within 5 days
OKRs to enhance employee dedication via communication optimization
OKRs to enhance and streamline Board operations
OKRs resources
Here are a list of resources to help you adopt the Objectives and Key Results framework.
- To learn: What is the meaning of OKRs
- Blog posts: ODT Blog
- Success metrics: KPIs examples
Create more examples in our app
You can use Tability to create OKRs with AI – and keep yourself accountable 👀
Tability is a unique goal-tracking platform built to save hours at work and help teams stay on top of their goals.
 1 Create your workspace
1 Create your workspace 2 Build plans in seconds with AI
2 Build plans in seconds with AI 3Track your progress
3Track your progress