OKR template to enhance data privacy and cybersecurity measures to safeguard sensitive information
Your OKR template
The objective also covers regular vulnerability assessments and tackling identified risks within specific timeframes. This involves prioritizing risks based on severity, setting timeframes for risk mitigation, and documenting the results of these assessments.
Furthermore, the OKR focuses on increasing employee participation in cybersecurity training programs by 25%. The initiatives for achieving this include creating engaging training modules, recognizing and rewarding active participants, and organizing awareness sessions about cybersecurity threats.
Lastly, the OKR aims to improve the incident response time by 10% for efficient mitigation of potential breaches. This will be accomplished by streamlining incident response processes, evaluating and improving incident response plans, providing comprehensive training, and implementing automation tools to quickly identify and contain breaches.
ObjectiveEnhance data privacy and cybersecurity measures to safeguard sensitive information
KRImplement a comprehensive data encryption system across all relevant platforms
Assess current data encryption measures and identify gaps for improvement
Develop and implement a standardized data encryption protocol for all platforms
Conduct regular audits to ensure consistent adherence to the data encryption system
Train employees on proper data encryption practices and its importance in data security
KRConduct regular vulnerability assessments and address identified risks within set timeframes
Quickly prioritize and address identified risks based on severity levels
Schedule regular vulnerability assessments according to established timelines
Establish set timeframes for risk mitigation and ensure timely execution
Develop a clear process for tracking and documenting vulnerability assessment findings
KRIncrease employee awareness and participation in cybersecurity training programs by 25%
Recognize and reward employees who actively participate in cybersecurity training
Create engaging and interactive modules for cybersecurity training programs
Organize lunch and learn sessions to promote employee awareness about cybersecurity threats
Send regular email reminders about upcoming cybersecurity training sessions
KRAchieve a 10% improvement in overall incident response time, ensuring timely mitigation of potential breaches
Streamline incident response processes and eliminate any unnecessary steps for faster response times
Regularly evaluate and improve incident response plans to enhance efficiency and effectiveness
Provide comprehensive training to all personnel involved in incident response procedures
Implement automation tools to expedite the identification and containment of potential breaches
How to edit and track OKRs with Tability
You'll probably want to edit the examples in this post, and Tability is the perfect tool for it.
Tability is an AI-powered platform that helps teams set better goals, monitor execution, and get help to achieve their objectives faster.
With Tability you can:
- Use AI to draft a complete set of OKRs in seconds
- Connect your OKRs and team goals to your project
- Automate reporting with integrations and built-in dashboard
Instead of having to copy the content of the OKR examples in a doc or spreadsheet, you can use Tability’s magic importer to start using any of the examples in this page.
The import process can be done in seconds, allowing you to edit OKRs directly in a platform that knows how to manage and track goals.
Step 1. Sign up for a free Tability account
Go tohttps://tability.app/signup and create your account (it's free!)
Step 2. Create a plan
Follow the steps after your onboarding to create your first plan, you should get to a page that looks like the picture below.
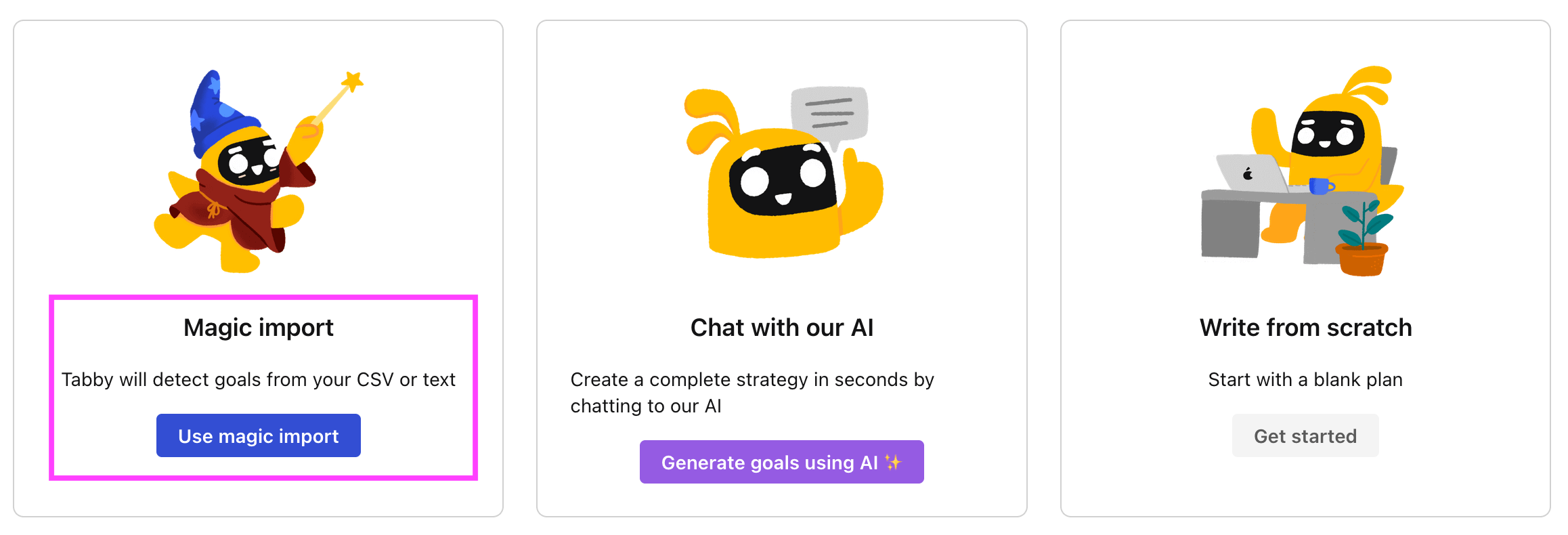
Step 3. Use the magic importer
Click on Use magic import to open up the Magic Import modal.
Now, go back to the OKR examples, and click on Copy on the example that you’d like to use.
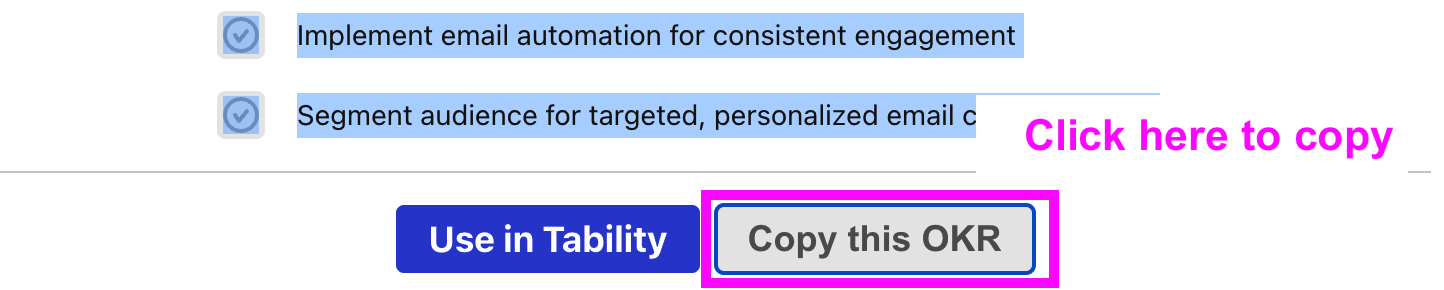
Paste the content in the text import section. Don’t worry about the formatting, Tability’s AI will be able to parse it!
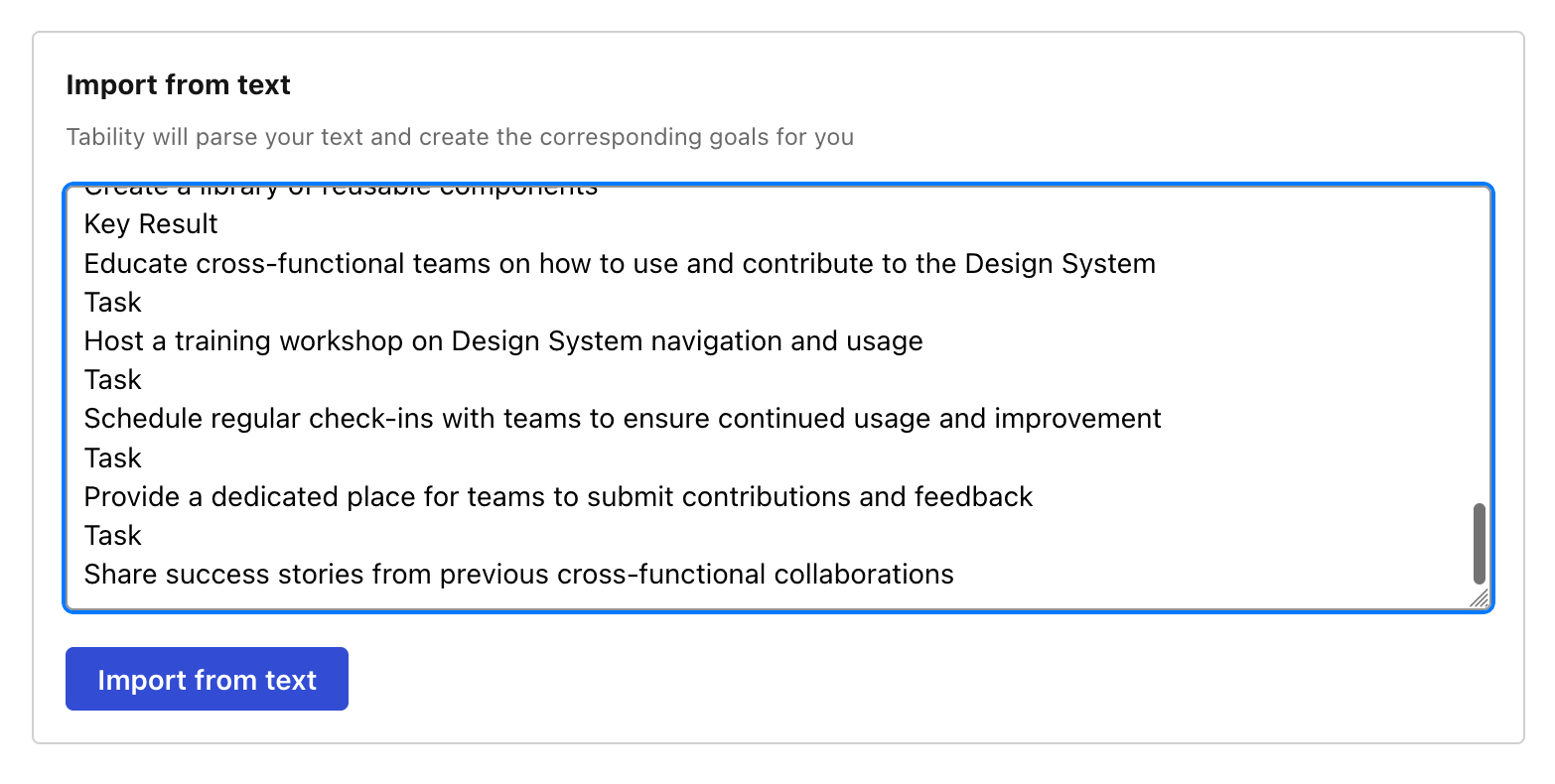
Now, just click on Import from text and let the magic happen.
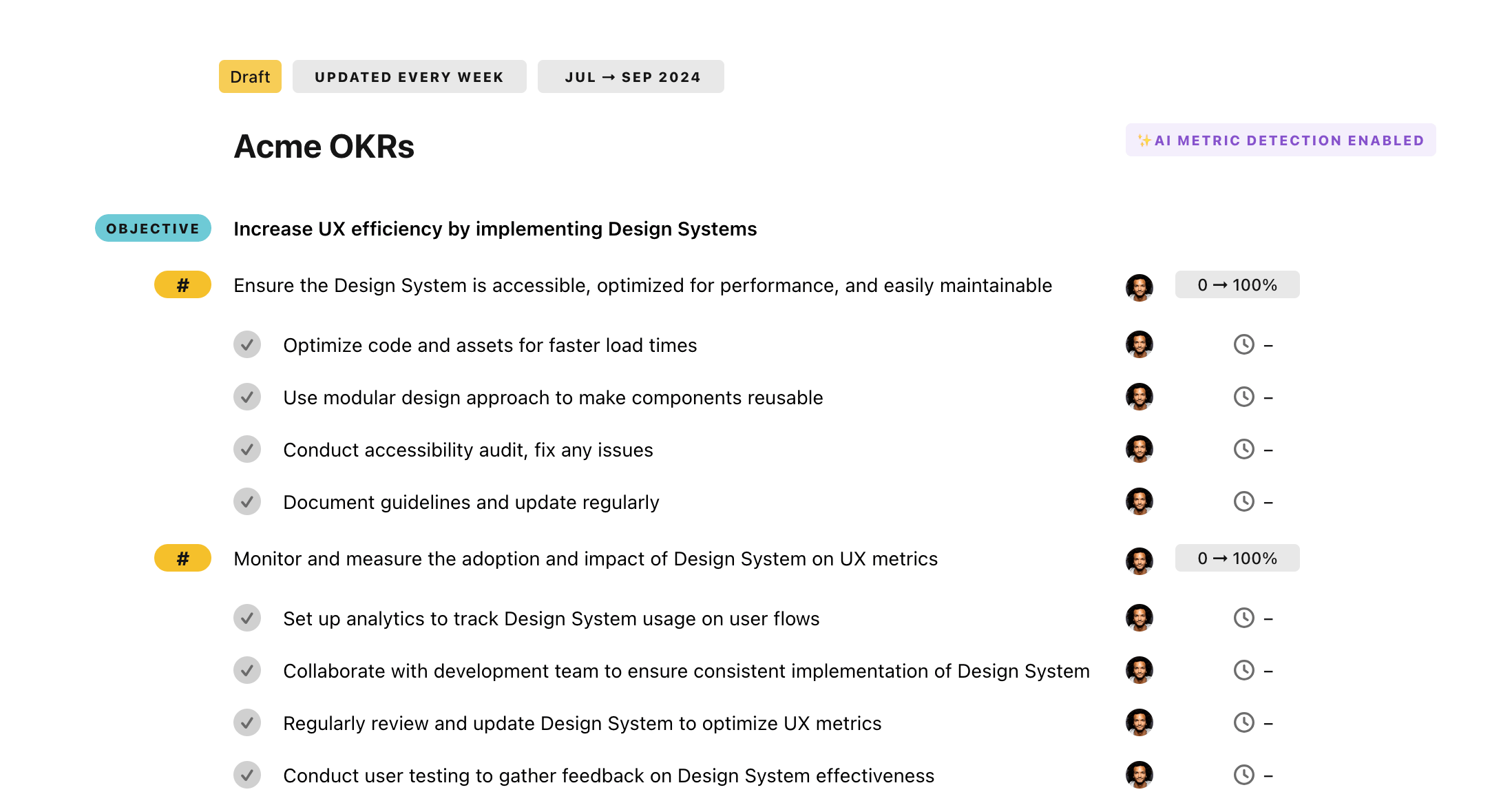
Once your example is in the plan editor, you will be able to:
- Edit the objectives, key results, and tasks
- Click on the target 0 → 100% to set better target
- Use the tips and the AI to refine your goals
Step 4. Publish your plan
Once you’re done editing, you can publish your plan to switch to the goal-tracking mode.
From there you will have access to all the features that will help you and your team save hours with OKR reporting.
- 10+ built-in dashboards to visualise progress on your goals
- Weekly reminders, data connectors, and smart notifications
- 9 views to map OKRs to strategic projects
- Strategy map to align teams at scale